Products

Who We Serve
April 10, 2014
There has been a lot of attention paid to the role that risk analysis and risk management play in protecting patient confidentiality in the last few months, and unfortunately much of that attention is the direct result of a significant upswing in breaches. According to data downloaded from the HHS publication of breaches affecting more than 500 people also known informally as the “wall of shame”, HHS reports that 931 breaches occurred in 2013, affecting nearly nine million patients. The Office for Civil Rights (OCR) also publishes its resolution agreements, and three of the last four provider-based agreements specifically call out the lack or inadequacy of a risk analysis as one of the key compliance issues.
Because of their concern regarding the inadequacies of the risk analysis currently in place at provider organizations, the HHS Office of the National Coordinator for Health Information Technology (ONC) and OCR released a security risk assessment (SRA) tool to help guide health care providers to conduct adequate risk assessments of their organizations. The tool can be downloaded here. The tool is primarily focused on small to mid-sized physician practices, but providers of all sizes can use it as part of their assessments of information security risks required by the Health Insurance Portability and Accountability Act (HIPAA) Security Rule and the core requirement to protect health information provided in the Meaningful Use / MIPS rule.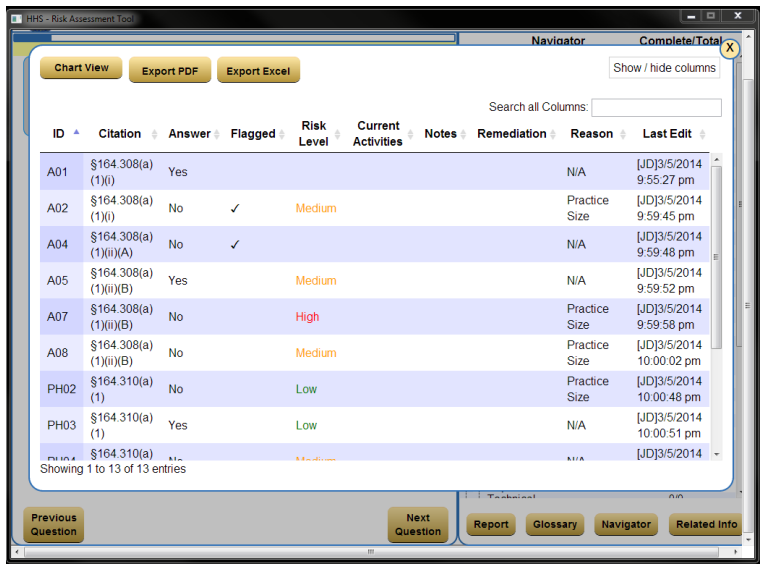
The tool, which is not mandatory, has three useful functions:
Users from the tool’s target market – small to mid-sized physician practices – will undoubtedly find the tool a useful guide to walking through an analysis of their practice’s risk, and many will find the exercise valuable in getting a detailed understanding of their organizational security position.
Users from larger organizations who have more knowledge, policies, and a larger number of affected systems and controls, are likely to find the tool’s design to be a limiting factor in their ability to properly document the scope of security controls they have in place. In particular, the tool lacks the ability to attach files such as policies to the assessment, and the blocks provided for data entry and reporting will not handle large quantities of text easily.
Those users with more experience with the risk analysis process will note that the tool is largely driven by questions about what controls are in place, instead of beginning with the more standard threat assessment process used by most security professionals and recommended by the government in several publications.
NIST publication 800-30 rev 1, the government’s guide to risk assessment presents a more standard (and admittedly more complex) approach to risk. That approach begins with the analysis of threats and the risks they represent, and then later addresses specific mitigating security controls, before turning to the assessment of risks.
The more HIPAA-specific NIST publication 800-66, An Introductory Resource Guide for Implementing the HIPAA Security Rule, also takes a threat-centric approach. The detailed steps presented in the risk analysis methodology portion of that document (beginning on page E-1 – page 90 in the PDF) places the steps “Identify Realistic Threats” and “Identify Potential Vulnerabilities” ahead of the identification and analysis of specific controls.
Evaluating Risks
The value of approaching risk from a threat and vulnerability standpoint is most clear when it comes time to evaluate risk.
Consider the evaluation of risk from a common vulnerability – the theft or loss of a laptop containing PHI — and it’s clear how to evaluate both the likelihood (hint: higher than most people think) and the severity (many breaches from computer loss/theft affect tens of thousands of records).
Compare this to the less clear evaluation of the risk presented if you answer “No” to question A14 in the SRA tool, “Is your practice’s security point of contact qualified to assess its security protections as well as serve as the point of contact for security policies, procedures, monitoring, and training?” The security rule clearly requires a named security official at 164.308(a)(2), and it’s obvious that the named individual needs to be competent. Do you answer this risk as very high likelihood, since by answering no, you’ve clearly indicated that you already have this risk, or do you answer it lower, based on your assessment of the likelihood of getting caught out of compliance?
The other step that many find useful in prioritizing the activities that come out of the risk assessment is a mathematical model that combines likelihood and significance rankings into a single ranked risk score.
Does the Security Risk Analysis Tool Tit the Mark?
The OCR Security Risk Analysis tool is a useful guide to exploring an analysis of security in the small to mid-size practices. However, larger organizations will likely find the tool’s documentation capabilities lacking and may prefer a threat and vulnerability driven analysis over a control-driven one. If this is the case, sample tools for this type of analysis are available for download over the internet, and are well described in the two NIST publications cited above.
Of course any approach to risk assessment is better than none at all. Larger organizations with a lack of dedicated and talented resources may find the tool just the thing to jump start their security efforts, but they also may wish to employ an experienced consultant to guide them efficiently through the risk analysis process.
We have published many blog posts in our HITpoint blog in the area of HIPAA security and privacy that may serve as additional resources for you. You may access them at https://www.medsphere.com/blog/
Phoenix consultants have been helping hospitals perform security risk analyses since 2003. Our methodology is detailed, practical, and well tested. For more information on our risk analysis services, visit our Services page or contact us!