Products

Who We Serve
February 10, 2021
Today, many hospitals count on external outsourcing services for a myriad of essential functions like revenue cycle management, health information management, IT support, data storage and security, housekeeping, and many other clinical and non-clinical functions. Many of these partners are business associates under HIPAA — and therein lies major potential security risks for hospitals. Relationships with diligent, qualified business associates have proven to be a boon to hospitals’ service quality and cost efficiencies. But data security and privacy breaches either caused by business associates or enabled by their deficiencies have exploded in recent years.
Every hospital and healthcare organization must protect itself through a well-defined and enforced business associate management program. Here’s what you need to know — plus a helpful infographic to summarize this critical issue.
Prior to the Omnibus HIPAA Rule of 2013, business associates (BAs) were not liable for their causing or contributing to breaches of security and patient privacy. The Omnibus Rule changed everything. It made both covered entities and business associates vulnerable to HIPAA penalties. It didn’t take long before the first BA HIPAA penalty was announced in 2015: a $650,000 fine against the Catholic Health Care Service of Philadelphia due to a 2014 theft of a single unencrypted smartphone that wasn’t password protected. CHCS was providing management and IT services to six skilled nursing facilities.
A summary look at HIPAA breaches related to business associates:

According to HIPAA Journal’s Healthcare Data Breach Statistics, 2020 was the 2nd worst year in terms of the number of breaches for BAs with 73 (the worst year was 2014 with 77). Two of the largest data breaches in 2020 were by BAs. Combined, they exposed information on more than 4 million individuals, and both were due to hacking/IT incidents, which are now the number one cause of data breaches.

Source: HIPAA Journal – Healthcare Data Breach Statistics, 2021.
A HIPAA compliant risk management program addressing outsourcing vendors and other business associates (BAs) has never been more critical.
Which of your hospital’s contractors are business associates under HIPAA?
Business associates include the people and companies that support a HIPAA-covered entity — in this discussion, healthcare providers in particular. Anyone who comes in contact or could potentially come in contact with Protected Health Information (PHI) is a business associate. The Omnibus HIPAA rule of 2013 says “business associates” include all vendors that create, receive, maintain, or transmit protected health information (PHI) on behalf of a covered entity, e.g. a hospital or payor. This includes your EHR vendor, other PHI-touching systems vendors, data storage firms, billing outsourcers, consulting firms, clinical service desks, lawyers, accountants, IT contractors, cloud storage services, email encryption services, web hosts, and more. It can even include your housekeeping and waste disposal outsourcers.
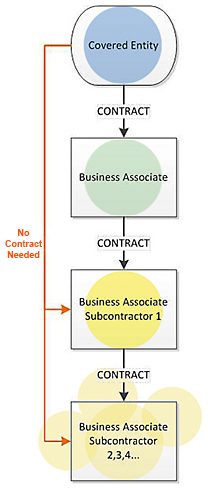 To complicate this scene even more, subcontractors of business associates that perform business associate functions are themselves business associates. As a result, the Omnibus Rule requires a chain of compliance starting with the HIPAA-covered entity, through the business associate, and ending with the lowest-tier subcontractor.
To complicate this scene even more, subcontractors of business associates that perform business associate functions are themselves business associates. As a result, the Omnibus Rule requires a chain of compliance starting with the HIPAA-covered entity, through the business associate, and ending with the lowest-tier subcontractor.
Just as covered entities are held responsible for breaches or violations of their business associates, so, “first level” or primary business associates are held responsible for the compliance of their subcontractors. As with covered entities, business associates are now subject to the same penalties for noncompliance. If a penalty is issued, it can range from $100 to $50,000 per violation (or record) with a maximum penalty of $1.5 million per year of violations of an identical provision.
Implementing a business associate risk management program
Bringing any external vendor into your hospital adds significant privacy and security risks. These are greatly compounded if the vendor uses subcontractors that also touch PHI.
Risk management can be divided into two broad stages: due diligence prior to engaging a vendor, and on-going monitoring and reporting. A cautionary note on due diligence: you may have narrowed your choice of vendors to just two or three, but if you haven’t performed a HIPAA risk assessment with finalists, you’re not ready to make a choice. HIPAA requires that you obtain satisfactory assurance of compliance in writing from all of your business associates.
Here are the essentials of a strong risk management program:
 addition to systems and process protections. You should assess facility access and other physical security measures implemented by the vendor. Ideally, this assessment should occur onsite, particularly if the vendor is to have significant access to your data.
addition to systems and process protections. You should assess facility access and other physical security measures implemented by the vendor. Ideally, this assessment should occur onsite, particularly if the vendor is to have significant access to your data.Many vendor/business associates don’t know that HIPAA covers them or what a BA designation means. This is partially because the covered entity representatives they work with don’t know much more than the vendor, and this aspect of the relationship never came up in the contracting process. It’s also because the covered entities have not established HIPAA-compliant procedures and/or accountabilities for their BA partnerships, and/or those procedures have not made it to the external contracting process. These activities cannot be compartmentalized; in other words, contracts with vendors who have the potential for touching PHI must get a go-ahead from the HIPAA security/privacy officer before they are signed. As OCR continues to audit hospitals and process increasing complaints of potential data mishandling, more hospitals are re-examining their BA management programs and their existing arrangements with external entities to ensure appropriate BA agreements are in place, monitored and enforced.
Our healthcare industry is learning the hard way. Cybercriminals are hammering it because they can. Negligence is way too commonplace, often among vendors that have no clue as to their HIPAA responsibilities. Our security and privacy environment is not yet as robust as industries like finance and manufacturing, but we can greatly strengthen it just by following the rules.
This was a long post, we know. So, to summarize, check out our infographic below on the risks of HIPAA BA relationships…share it with your colleagues AND your business associates!

For more information on HIPAA risk management, please contact us.