Products

Who We Serve
August 8, 2018
Have you noticed? We haven’t read shocking news of record-breaking security breaches, in fact not since 2015-2016. Remember Bon Secours Health System where the information of 655,000 patients was compromised via the internet? Or the breach at 21st Century Oncology Holdings that hit more than two million patients across 181 cancer treatment centers? A cyber attack on Banner Health affected 3.6 million people, and NewKirk Products, a business associate, was hacked to the tune of 3.5 million affected individuals. According to HHS’ Wall of Shame, over 113 million people were hit in 2015 by breaches of their personal data, and in 2016 more than 27 million patient records were impacted. But, in the whole of 2017 “only” about 4.7 million people were victimized, a four year low. This may seem like good news, but before we get too comfortable with our seemingly safer data security today, here’s the story behind the story — and it isn’t pretty.
Many big healthcare cybersecurity news stories have focused on ransomware, the frightening new weapon used by hackers to stop healthcare computing operations cold in order to extort bitcoin payoffs. Though ransomware attacks received a lot of press, it is clear that patient identity theft remains the most dangerous threat facing the healthcare industry. Even back In 2016 the HIMSS Cybersecurity Survey reported that identity theft had become cyber criminals’ strategy of choice because of patient data’s sheer marketplace value.
This year’s HIMSS 2018 Cybersecurity Survey of 239 information security professionals from various healthcare organizations reported a similar predominant trend of identity theft. The number of individuals impacted by security incidents decreased, but the number of incidents has not slowed down. Over 75% reported that their organizations had experienced a significant security incident in the last year. “If anything…significant security incidents will continue to grow in number, complexity, and impact,” according to the report.

Externally based incidents have gotten the most press. HIMSS reports that the three greatest perpetrators of recent significant security incidents are online scam artists (phishing exploiters), negligent hospital insiders, and criminal hackers. These are followed by malicious insiders and social engineers — hackers who play fraudulent tricks on insiders using tools like phone calls and social media.
If we look a little deeper at the numbers below it becomes clear that our hospital insiders — physicians, nurses, IT and other staff — are complicit, mostly inadvertently (a few, deliberately), in at least 70 percent of security incidents. These would include staff or business associates that are taken in by online scam artists and criminal social engineers, in addition to negligent insiders. Take a look at this screenshot from HIMSS’ 2018 report:
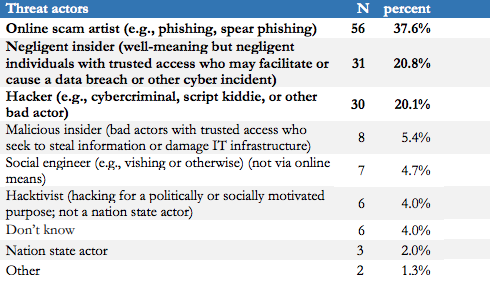
We must squarely look at the unfortunate role of our well-meaning hospital insiders in the dangerous state of healthcare cybersecurity today and step up protections:
It’s clear that healthcare organizations must do more to reduce these internal vulnerabilities, as well as prevent external hacking in its many ever changing forms.
The somewhat good news: About 85% of respondents say that their organizations have increased the resources needed to manage cybersecurity concerns. The following graph shows the percentage of IT budgets allocated to cybersecurity in 2018.
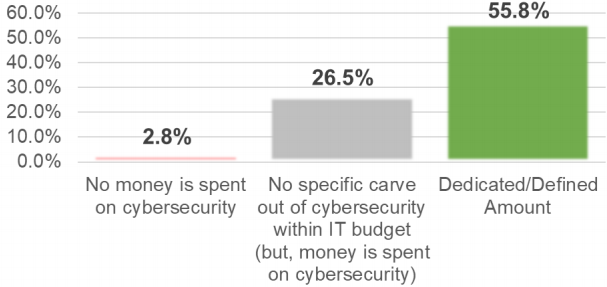
We can all agree that any increased expenditures and efforts to protect our hospitals’ data are important actions, but we all should be concerned that the overall hospital industry’s response to the abundance of security risks has not been greater or more clearly defined as priorities in IT budgets.
Specific efforts focusing on internal vulnerabilities should be especially high priority. Potential issues like the following must be hit hard:
Most predictions indicate healthcare is headed into a period of increased cybersecurity risks in 2019 and beyond. Hospitals, other providers and business associates should complete a security risk analysis soon, if they haven’t yet conducted one this year. As always, well-qualified internal IT security professionals or an objective third part security professional must lead the process. Then they should calibrate your organization’s unique risks against potential costs — including the privacy costs of patients — to plan ahead for technical and social protections that will minimize your vulnerabilities and thwart the cyberthreats that are sure to come.
________________________________
If you need the security knowledge and expertise of certified specialists with over 20 years of hospital privacy and security experience, contact us.